Catégories: "Informatique"
Debian & LLVM events
Janvier 17th, 2014Being a bit hyperactive, I have been involved in the organization of two events. I am the main organizer with Alexandre Delanoë of the Mini Debconf 2014 in Paris, January 18 & 19th.
The (great) planning is available here:
https://france.debian.net/events/minidebconf2014/
Saturday morning presentations will be general public, the beginning of Saturday afternoon will be used by the Debian France association to vote the new status (1901 law and Debian Trusted Organization).
Sunday will be more focused on Debian itself.
During the week end, I will be talking about the Debile project, the finance of Debian France and be part of the round table on compiler selection for Debian.
The (mandatory) registration should be done on the Wiki or meetup.com
In parallel, with Tobias Grosser, we organized the LLVM devroom track at FOSDEM (Bruxelles), February 2nd (Sunday).
The schedule is a mix between core developers, third party software using LLVM / Clang and academic users.
https://fosdem.org/2014/schedule/track/llvm/
I will be talking on how to become a LLVM contributor.
Both events should be recorded.
Debian France shop
Janvier 15th, 2014During the month of December, we have been working with folks from En Vente Libre to create a shop with Debian products:
http://www.enventelibre.org/debian
We have now a shop with plenty of Debian products. The design has been done by Ahmet DEMIR. Most of them are already known by the community (they were sold during FOSDEM or various Debconf) like the Buff, Swiss Army knife or the classical polos.
But, t-shirts based on Wheezy theme are brand new:
They are available in three colors:
* Red
* Blue
* Grey
For now, the website is only French, an English version might come in the future.
Some thoughts concerning LLVM & Clang and their evolutions: Release of LLVM & Clang 3.4
Janvier 15th, 2014We just released LLVM & Clang 3.4 (already available in Debian Jessie and Ubuntu Trusty). The clang new release introduces some more warning and error detections. The point of the blog post is not to detail the changes (LLVM / Clang) but more to take a step back on the LLVM and Clang toolchains, usages and dissemination.
For the last couple years, I have been presenting our work on the Debian side to make Clang part of the Debian infrastructure. I add the chance to speak at many events (Debconf 12 & 13, FOSDEM 2013, Linux Plumbers 2013, Distro recipes, etc). I even had Linus Torvalds attending to one of these talks (and proposing new approach). I had many feedback from the Debian/Ubuntu communities but also from other communities.
More and more projects are using Clang as part of their workflows, in term of development, production and QA. For example, some of them are running continuous integration using clang instead of gcc, others are running scan-build (Wireshark or LLVM itself) or Address Sanitizer (asan) (Firefox for example), etc.
More and more actors are moving from gcc to clang for their developments (Sony with their PS4, Chrome under Mac OS X, Apple, the Linux Kernel with the LLVMLinux project, FreeBSD, etc).
I stopped counting the number of times when people answered me "Yeh, I am now using Clang" when I said I am involved upstream.
In parallel, more and more projects are using LLVM as a backend or computing engine and, in the meantime, getting more and more attraction (not because they are based on LLVM but just because they are great projects). For example, Mesa (llvmpipe), Julia, Rust, Emscripten or Native Client (NaCL) are excellent examples of this. The two last are excellent proofs that LLVM based technologies have an impact which goes further than geek-tools and will be used on a daily basis by millions of users.
I also saw an interesting and growing number of new projects using libclang and libTooling. My feeling is that the lack of plugin capabilities in gcc for a long time and, now, its current complexity limited the innovation in term of compilation capabilities, analysis and fun tools. The features and the quality of this library are enabling new developments and I am sure we will see more and more excellent tools based on this library during 2014.
For example, the LLVM toolchain ships Clang modernize and clang format and some cool projects like include-what-you-use, DXR, OCLint or creduce are emerging.
Thanks to this great competition, gcc is also improving (ASAN, JIT, better warnings, etc), remaining still relevant as before. No doubt that 2014 will be a great year for compilers.
Include What You Use - Yet a new cool tool in Debian.
Septembre 8th, 2013iwyu (Include What You Use) has just been accepted in Debian.
This tool, based on LLVM/Clang, checks the headers of a C/C++ file. It will detect which include directives are useless, what could be improve and add comments to explain why #include are there.
Let's take this C file:
#include <stdio.h>
#include <malloc.h>
#include <limits.h>
int foo(void) {
fprintf(stderr, "an error\n");
return INT_MAX;
}
$ iwyu foo.c
will return:
foo.c should remove these lines:
- #include <malloc.h> // lines 2-2
The full include-list for foo.c:
#include <limits.h> // for INT_MAX
#include <stdio.h> // for fprintf, stderr
---
About optimization flags in software
Septembre 6th, 2013Following a thread on the Clang mailing list, I did a quick analysis of the optimization flags used to build C or C++ code.
I used a rebuild result from last mid July of all Debian native packages (meaning that I don't have the log of full Java, Python or other packages without native code) and wrote a small script to count all their occurrences.
By default, deb packages uses the command "dpkg-buildflags --get CFLAGS" which will set the optimization level to -O2. However, many packages and upstream build systems do not respect such flags.
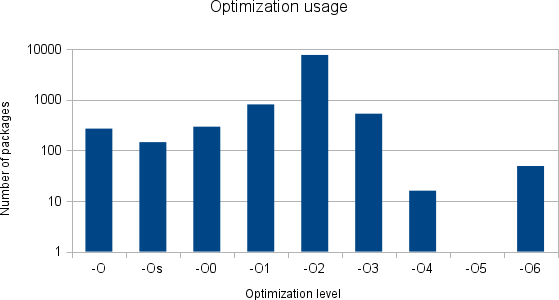
On 10320 binary-only packages (in total, Debian has around 19000), the results are the following:
| Optimization level | Number of occurrences | Number of packages |
|---|---|---|
| -O | 35597 | 269 |
| -Os | 30849 | 145 |
| -O0 | 13993 | 294 |
| -O1 | 25494 | 809 |
| -O2 | 995803 | 7685 |
| -O3 | 106048 | 531 |
| -O4 | 1402 | 16 |
| -O5 | ||
| -O6 | 6935 | 49 |
Since a graphic talks more than numbers (note that the Y axis is logarithmic):
Disclaimer:
Some packages are using several optimization flags during the same build.
Some packages are not showing the full command line (see jessie release goal: verbose build logs)
The results might be approximate since I am basically grepping "-OX " on the log files.